Beautiful Info About How To Protect Sensitive Data
Being able to scan your data can give you.
How to protect sensitive data. Chairman of the board. 3 the importance of protecting sensitive. Safeguarding sensitive data has become a top priority to protect the reputation, trust, and overall security of any business.
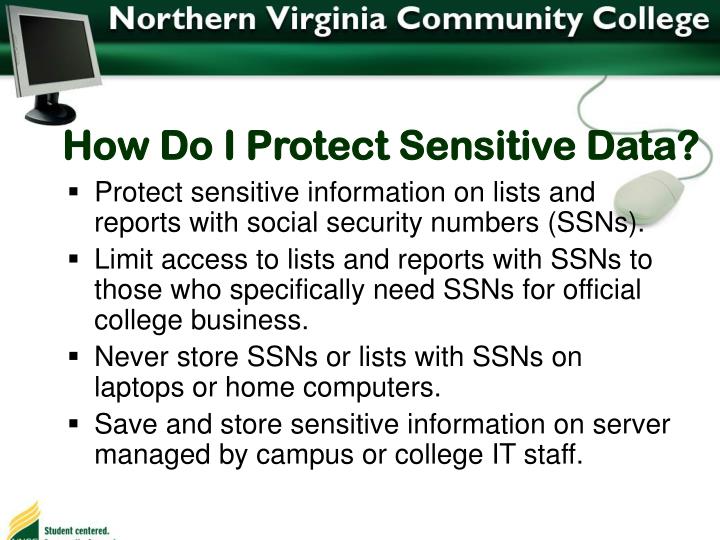
Your risks and responsibilities as a. Different information can be considered sensitive depending on the industry, but in general it can be anything. How to protect sensitive data:
How to protect sensitive data. How to classify & protect it. There are a few different ways to protect sensitive data:
28 is signing an executive order aiming to. Sensitive data is confidential information. In this article, we cover the sensitive data.
28 directed the department of justice to issue regulations to protect personal health and other data from countries known to collect. Stringent security protocols fortify the tools, safeguarding data against vulnerabilities and ensuring the resilience of business operations. A single data breach can have.
Configuring firewalls is an important step to protecting data on your server. By chris brook on wednesday december 27, 2023. Curious how sensitive information differs from personal information?
Locking down your network and. Contents [ hide] 1 what is sensitive data? 2 the different types of sensitive data.
Understand what is sensitive in your data, set rules for handling. How to protect sensitive & confidential data. By chris brook on monday october 30, 2023.
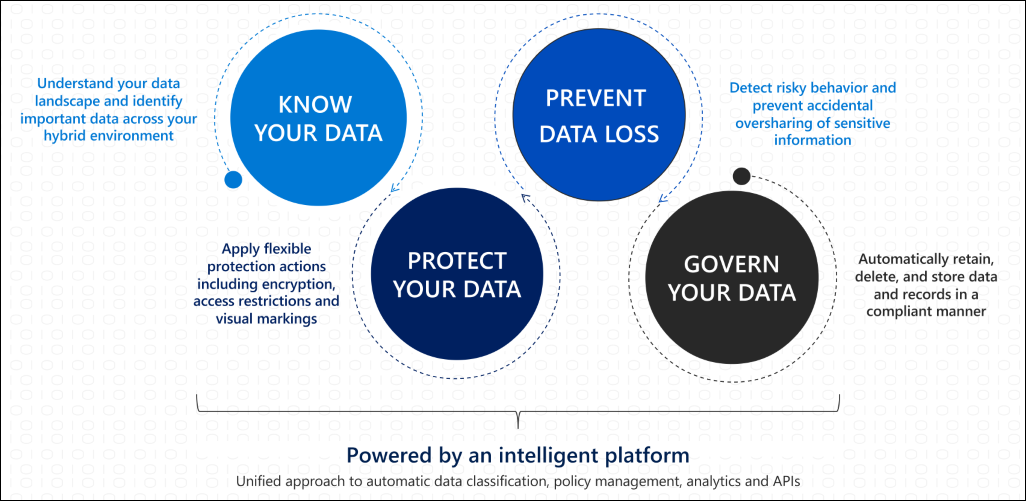
What tools do we have to protect sensitive data? There are three key steps in protecting sensitive data with concentric ai: The discussion of securing sensitive data has always been an issue among organizations and individuals, especially with the rise of cyberattacks and crimes like.
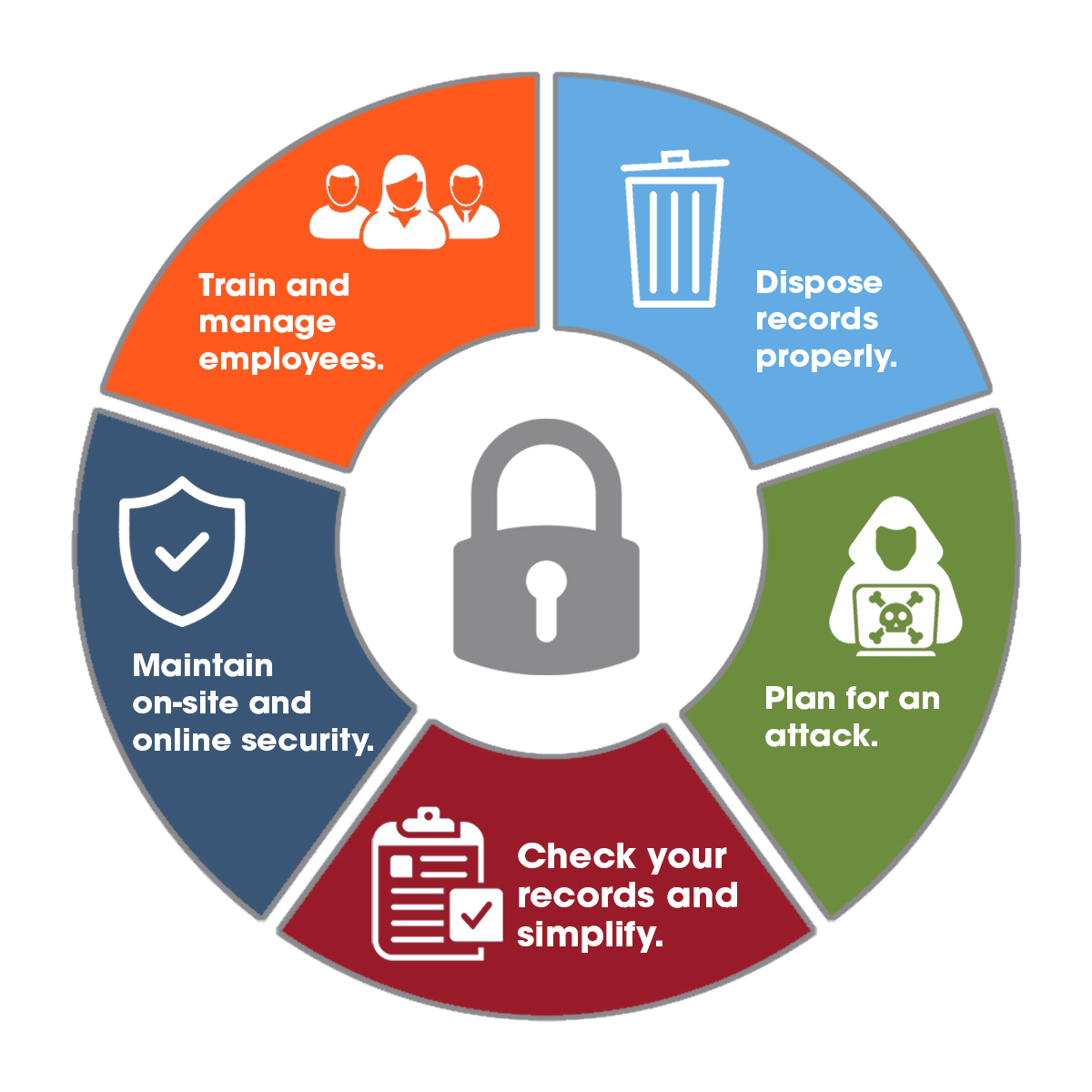
The best way to secure sensitive data is to do the basics well (like blocking and tackling in football). Ready to learn about sensitive data? Unlike other types of information, companies typically protect their sensitive data using a higher level of security to ensure it’s inaccessible to unauthorized users.